How API Keys Work
When you create an API key:- The key copies the service account’s roles
- The key’s role are set and cannot be changed
- Your service uses this key to make API calls
- Flexprice checks the key’s permissions for each request
Permissions Are Set at CreationOnce an API key is created, its permissions don’t change.
To get new permissions, create a new API key with required.
Creating an API Key
Via Dashboard
Navigate to Developers > API Keys and click Create to open the API key creation dialog.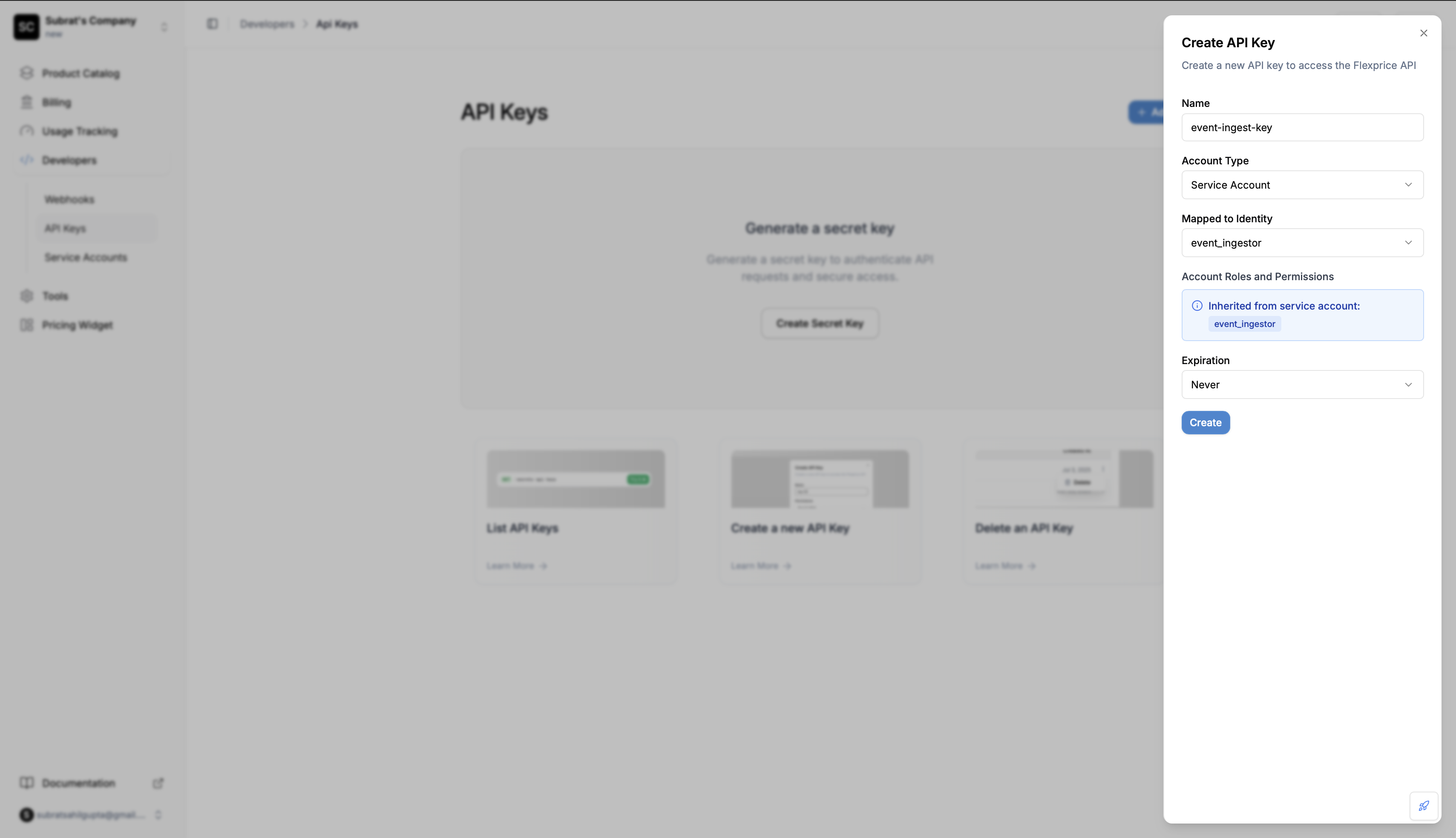
- Name: Give your API key a descriptive name
- Account Type: Select between User Account or Service Account
- Mapped to Identity: If Service Account is selected, choose which service account to use
- Expiration: Set when the key should expire (or select Never)
- Click Create
Via API - For Your Own Account
Create an API key for yourself:For a Service Account
Create an API key for a service account:Response
Storing API Keys Securely
✅ Good Practices:- Store in environment variables
- Use secret management services (AWS Secrets Manager, HashiCorp Vault)
- Use Kubernetes Secrets for containerized apps
- Store in your CI/CD platform’s secret storage
- Committing to Git repositories
- Hardcoding in your application code
- Sharing via email or messaging apps
- Storing in plain text files
Request Parameters
A descriptive name to help you identify this key later.Examples:
"Production Event Service", "Staging Analytics", "Development Integration"The ID of the service account to create the key for. If not provided, creates a key for your own account.
Understanding Roles and Permissions
Example 1: Event Ingestor Role
Service Account has:event_ingestor role
API Key inherits: event_ingestor role
What happens:
- ✅ Can send events
- ❌ Cannot read events (403 Forbidden)
Example 2: Multiple Roles
Service Account has: Bothevent_ingestor and event_reader roles
API Key inherits: Both roles
What happens:
- ✅ Can send events (from
event_ingestor) - ✅ Can read events (from
event_reader)
Best Practices
Use Descriptive NamesName your keys clearly:
"production-event-service", "staging-analytics", "dev-integration"Rotate Keys RegularlyCreate new API keys and delete old ones every 90 days.
One Key Per ServiceCreate separate API keys for each service or integration, even if they use the same service account.
Troubleshooting
API Key Not Working
Symptom: Getting “Unauthorized” errors when using the API key. Possible Causes:- API key format is incorrect
- API key has been deleted
- Using the wrong key for the environment (test vs. production)
- Check if the key still exists
- Make sure you’re using the correct environment
Getting 403 Forbidden Errors
Symptom: API calls return “Forbidden” errors. Possible Causes:- The service account doesn’t have the required role
- The API key was created before roles were assigned
- The role doesn’t include the permission you need
- Check what roles the API key has
- Verify those roles include the permission you need
- If roles were recently added, create a new API key with the service account associated with required roles
Lost API Key
Symptom: You didn’t save the API key when you created it. Solution: API keys cannot be retrieved after creation. You need to:- Create a new API key for the same service account
- Update your service with the new key
- Delete the old key

